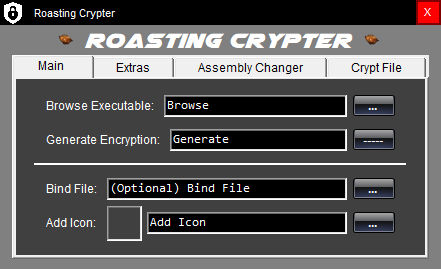
A .NET crypter, for all .NET programs. Encyrpts strings and data to prevent deobfuscation and cracking of your programs. The Roasting Crypter allows users to bind any type of file to the chosen executable application. This crypter also allows its users to inject the chosen executable application file into a number of Base Microsoft Windows required application files! Roasting Crypter has the option to add the chosen executable to the Microsoft windows Registry which can create a persistent running executable application file. Lastly, the Roasting crypter allows users to set the executable to spread through LAN connection, USB connection, and Zip/Rar files! This is a great tool for any of your needs! Because of all the different options this complex crypter has, it took some time to create it, but it works, and it works well. Let me know if you have any problems! Enjoy!
What is Encryption?
In cryptography, encryption is the process of encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can decipher a ciphertext back to plaintext and access the original information. Encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor.
For technical reasons, an encryption scheme usually uses a pseudo-random encryption key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users.
Historically, various forms of encryption have been used to aid in cryptography. Early encryption techniques were often utilized in military messaging. Since then, new techniques have emerged and become commonplace in all areas of modern computing. Modern encryption schemes utilize the concepts of public-key and symmetric-key. Modern encryption techniques ensure security because modern computers are inefficient at cracking the encryption.