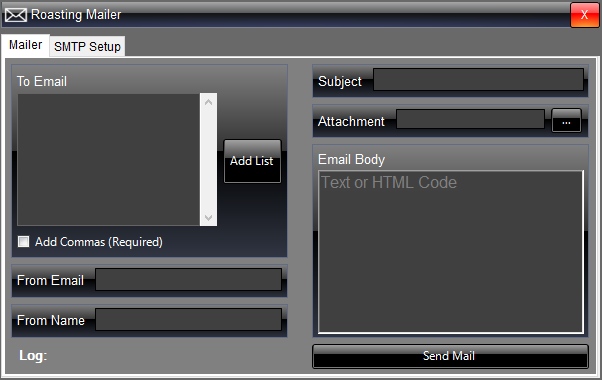
A semi complex Spoof emailer. No bugs or errors, that I can find, if you find any please let me know so I can do a quick fix
Also, for the smtp setup, I found that either using AWS with an smtp service or smtp2go works really well. I have delayed release of version 3.0 of this email spoofer because of problems that haven arose. As stated on my home page, I am currently low on funding and with Roasting Mailer version three, I will be releasing it to the Microsoft Windows store with ads running on it. This will ensure that the program is works the same way but also can generate the creator (Me) revenue so that I can continue to upload more open source projects! So please bear with me and Enjoy this release for now!
What are the technical details of email spoofing?
When a Simple Mail Transfer Protocol (SMTP) email is sent, the initial connection provides two pieces of address information:
MAIL FROM: - generally presented to the recipient as the Return-path: header but not normally visible to the end user, and by default no checks are done that the sending system is authorized to send on behalf of that address.
RCPT TO: - specifies which email address the email is delivered to, is not normally visible to the end user but may be present in the headers as part of the "Received:" header.
Together these are sometimes referred to as the "envelope" addressing – an analogy to a traditional paper envelope. Unless the receiving mail server signals that it has problems with either of these items, the sending system sends the "DATA" command, and typically sends several header items, including:
From: Joe Q Doe <[email protected]> - the address visible to the recipient; but again, by default no checks are done that the sending system is authorized to send on behalf of that address.
Reply-to: Jane Roe <[email protected]> - similarly not checked
and sometimes:
Sender: Jin Jo <[email protected]> - also not checked
The result is that the email recipient sees the email as having come from the address in the From: header. They may sometimes be able to find the MAIL FROM address, and if they reply to the email it will go to either the address presented in the From: or Reply-to: header, but none of these addresses are typically reliable, so automated bounce messages may generate backscatter.
Although email spoofing is effective in forging the email address, the IP address of the computer sending the mail can generally be identified from the "Received:" lines in the email header. In malicious cases however, this is likely to be the computer of an innocent third party infected by malware that is sending the email without the owner's knowledge.